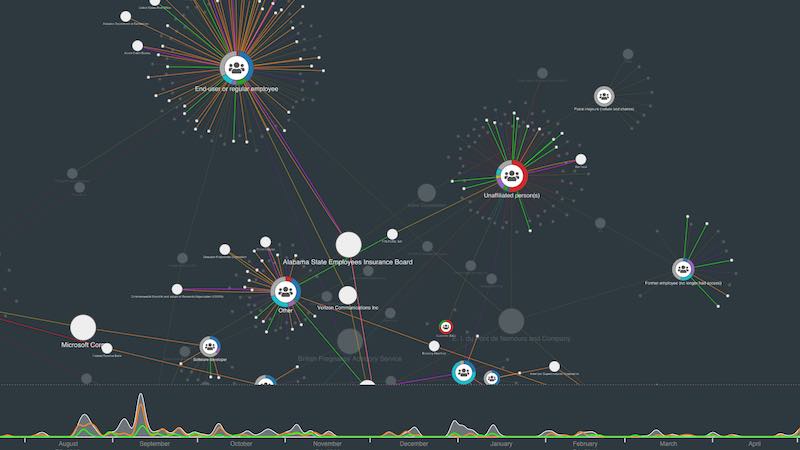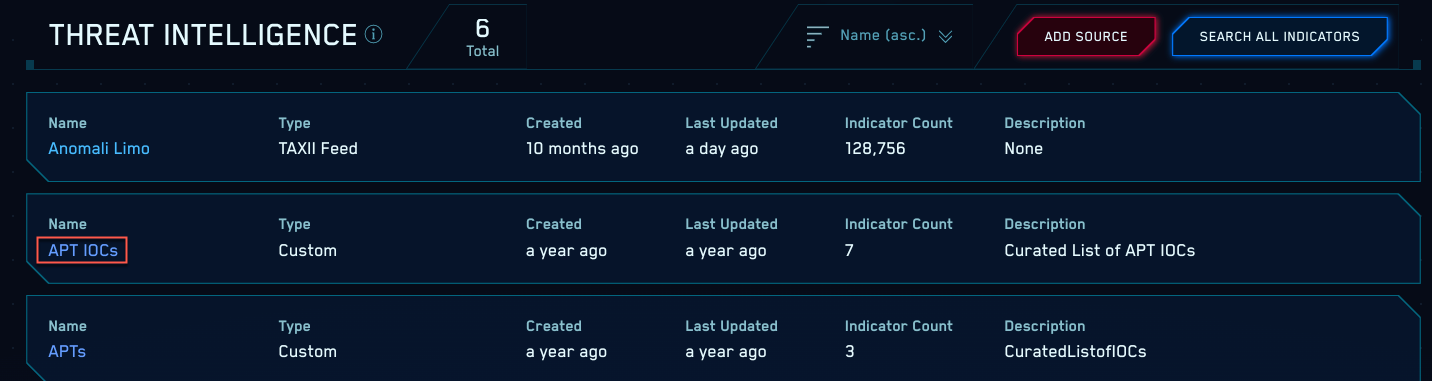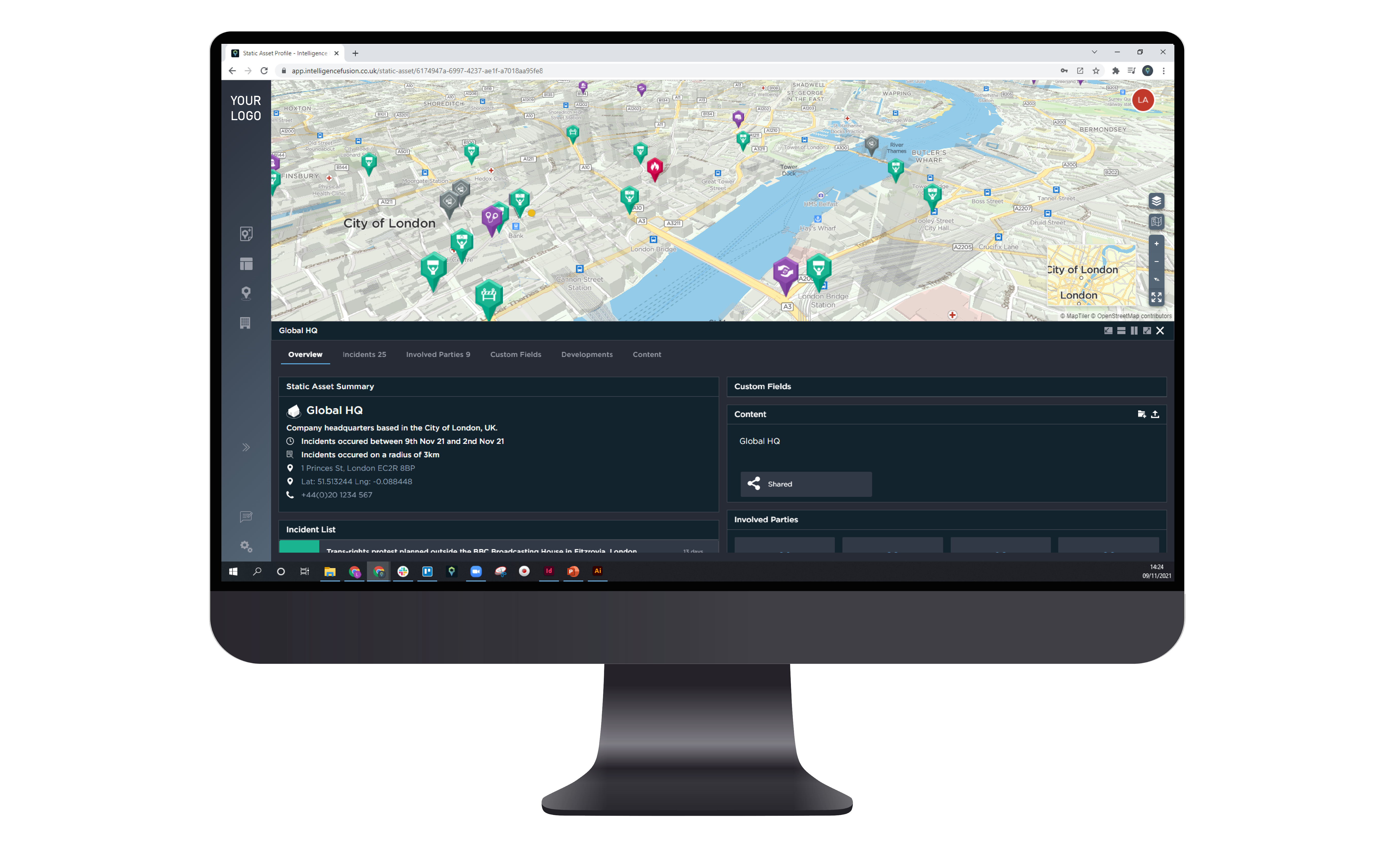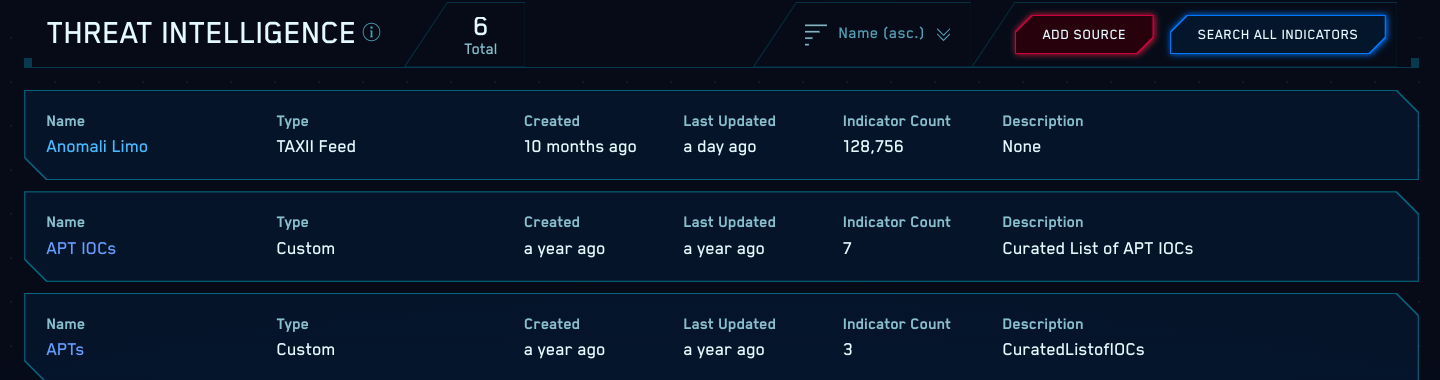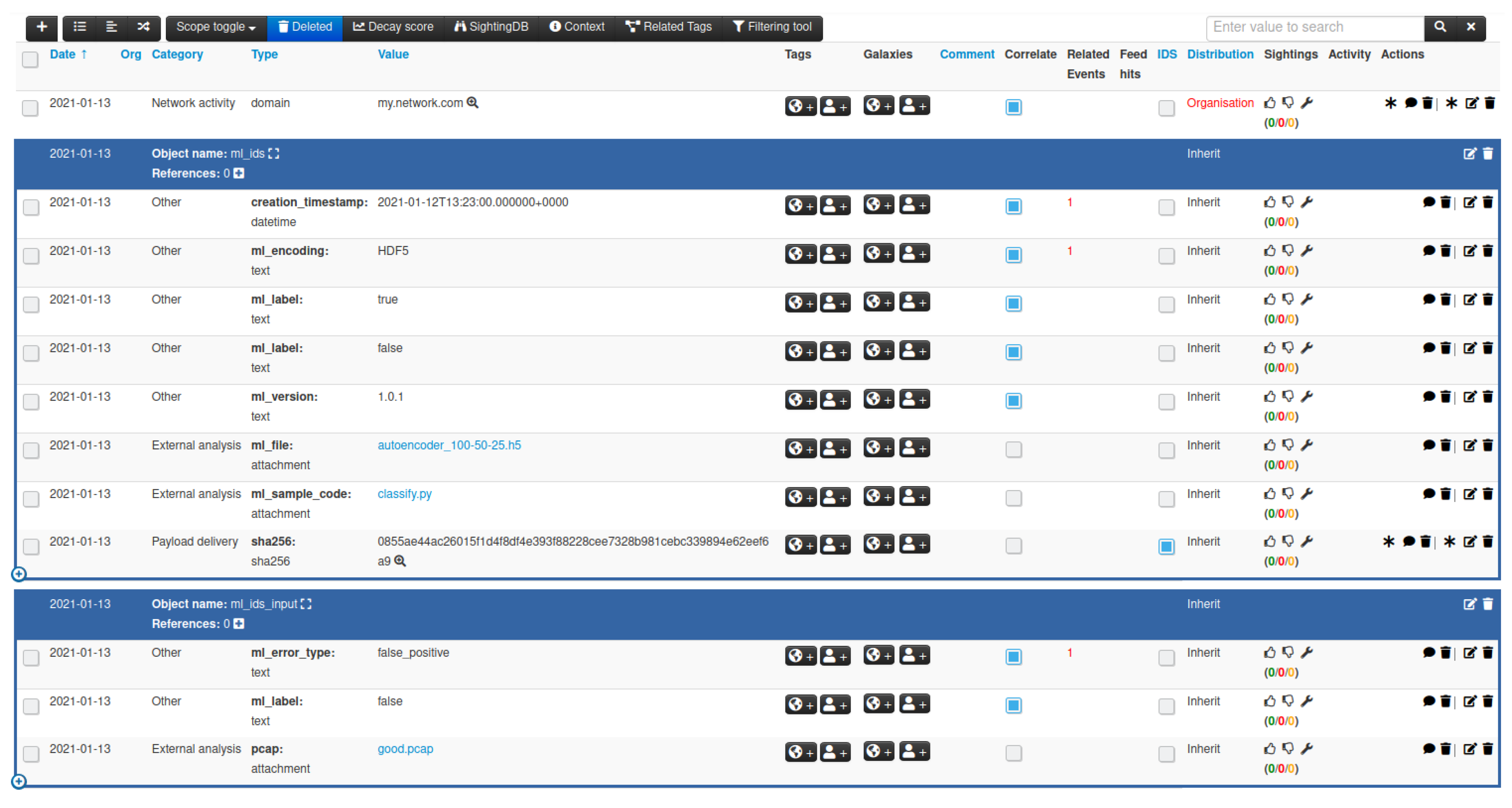
JCP | Free Full-Text | Sharing Machine Learning Models as Indicators of Compromise for Cyber Threat Intelligence

How to automate the import of third-party threat intelligence feeds into Amazon GuardDuty | AWS Security Blog

Full Cycle: Blending Intelligence Requirements and Custom Dissemination Tools to Drive Operations - YouTube

Full Cycle: Blending Intelligence Requirements and Custom Dissemination Tools to Drive Operations - YouTube

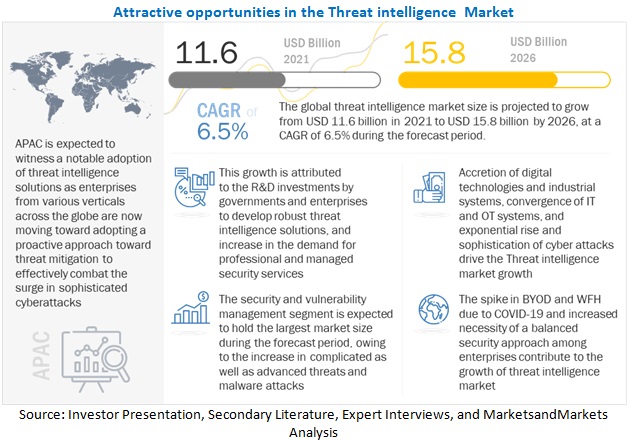
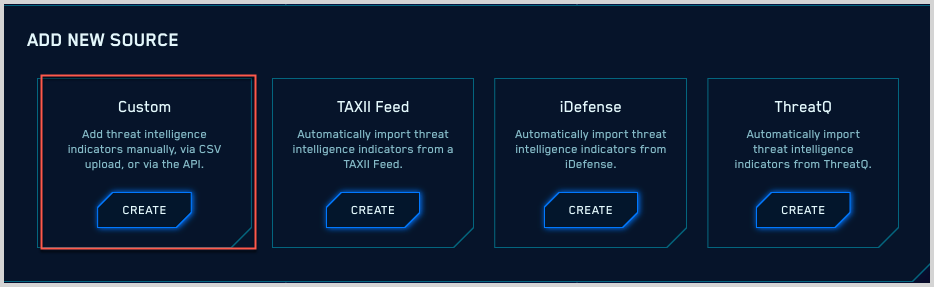

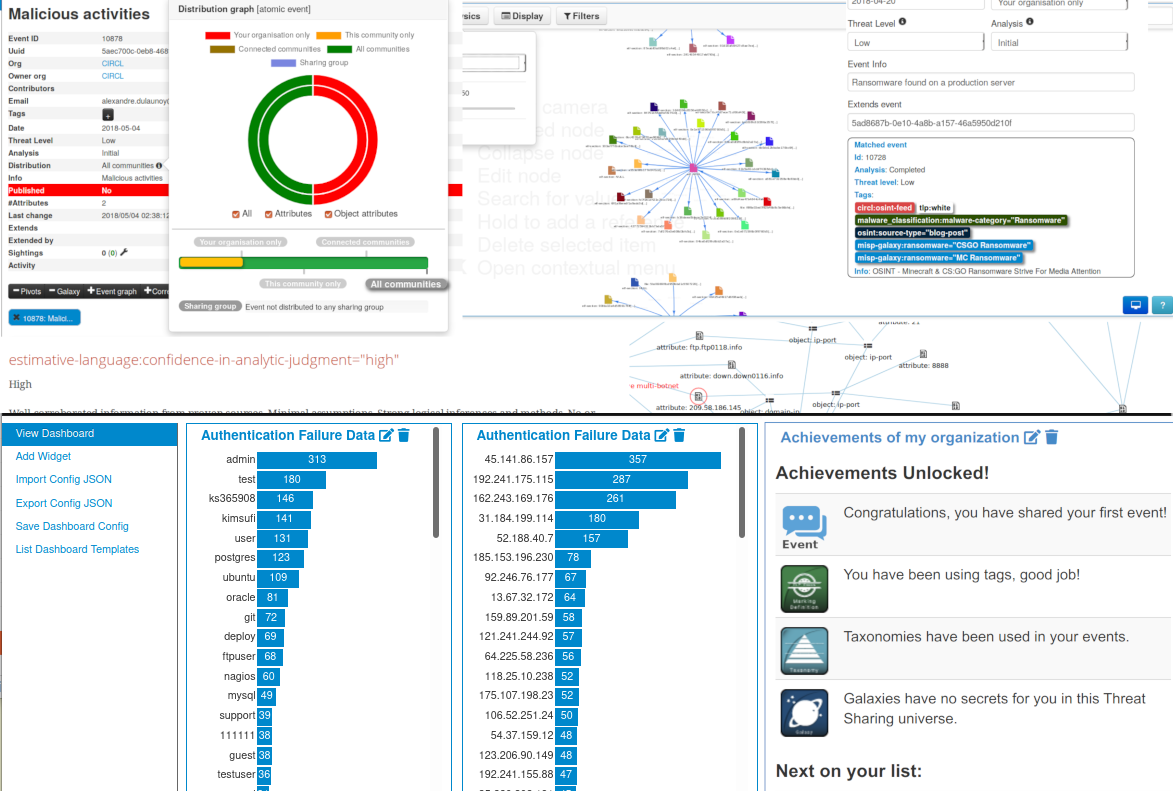


![What is Cyber Threat Intelligence? [Beginner's Guide] What is Cyber Threat Intelligence? [Beginner's Guide]](https://www.crowdstrike.com/wp-content/uploads/2019/07/crowdstrike-threat-intelligence-areas.png)